 Careful now.
Careful now.
Scary moment this week when I got an email from a very trusted friend with a google docs attachment. Just click on it and load up your email address — and password, of course.
Habits rule, and my fingers starting typing out the email address and passwords. Oops. Spent the next two hours changing all my login passcodes.
According to Wikipedia,
Phishing is the act of attempting to acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication.[1][2] Communications purporting to be from popular social web sites, auction sites, banks, online payment processors or IT administrators are commonly used to lure unsuspecting public.
Just a click away
We spend a good amount of time fixing student computers that have been compromised by viruses or hijackers. It all starts with a click.
Here’s the phishing attack that was sent through a friend’s email, which was hacked. It was sent to all the contacts in the account:

note the “url” or web address:
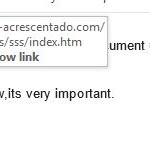
Not who is claims to be, is it? That website has been shut down, and it is likely that the owner never even knew it was being used this way. Hackers will hijack one website and use it to pretend to be another, all in order to gain access to logins. Here’s an article on this particular “phishing” scam:
Google Docs Phishing Email Scam
Google account users, beware of the phishing email messages below that were designed to steal your Google user name and password. If you receive any email message appearing as if it came from a friend or family member, asking you to view a document that was uploaded to Google Docs or Google Drive, please delete this message. This is another malicious attempt by hackers and scammers to steal your Google account information so that they can rob you or sell your information to other scammers.
What do they get from it?
Well, here’s a short list:
- use your email address for more phishing attacks
- login to all your accounts that might be linked to this email address, including bank accounts, e-wallets, retailer websites, etc. Anything associated with your account. Once they’re in your inbox they can see everything you do.
- set up fake accounts using your email address.
- send out emails with ads, obscene materials, and links to viruses
Why do they do all this? Just like those “Nigerian Prince” scams — they do it because it works.
On our website we get hundreds of hits daily from scammers, and our servers get nightly hack attempts. It’s amazing, but that’s what they do. They seek out random sites and try to take them over. Once in, it’s now a toy for their games.
Look before you jump!
The “enter button” on your keyboard is final. There’s no eraser, not delete after the fact. The best you can do is to be aware.
- Look both ways before crossing the street.
- Look before jumping.
- Don’t take candy from strangers.
Your mother’s old advice works just as well in the digital age as it did in the neighborhood where you grew up.
Trust but verify the URL
The name of the website just prior to the “.com” is your key. Subdomains are those name that precede the website name, such as “mail.” or “blog.” (such as we use). The names that follow the slashes / are directories of that main website. Even if you see “google” or some name you trust, make sure it is the main domain and not a directory or subdomain.
Here are some (fake) examples:
- www.google.com/post.php?post=415151action=013f&asdflkj
- mail.google.com/post.php?post=415151action=013f&asdflkj
- google.phishingweb.com/post.php?post=415151action=013f&asdflkj
No. 3 is the bad one. Check your web address bar and make sure it’s legitimate. Please, because every time one of you makes a wrong click, it’s another headache for the rest of us.
– Michael